Updated on August 6, 2020
Secure Communications Can Be Provided By VPN
A Virtual Private Network is a tool that can be used for personal media and business both. It acts by establishing a secure network but creating a virtual tunnel that is encoded by a public network, usually the Internet. Businesses used to hire private lines to connect their branch office including the offices that are settled abroad, and the amount they spend is very large due to the wide range of availability of network connectivity is very expensive.
Apart from business or corporate use, a Virtual Private Network (also known as 가상 사설망 in the Korean language) connection can also be used personally by consumers, in order to use applications that might not be allowed by your ISP, such as VoIP, or may be blocked by a firewall, or web site bypass censorship restrictions caused by a country.
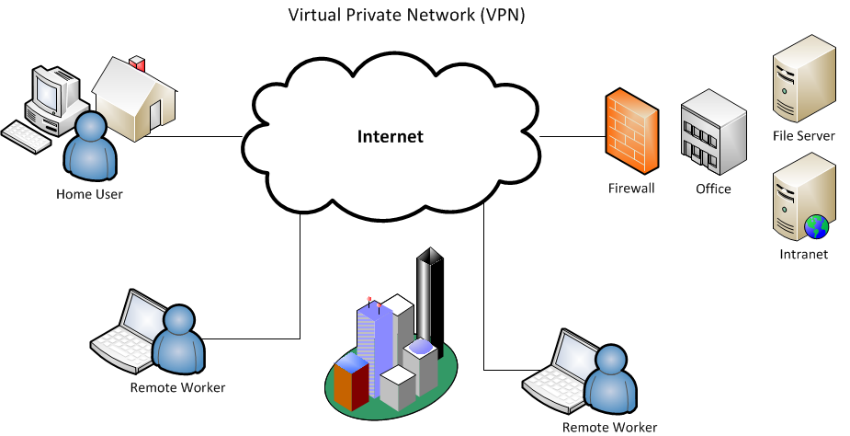
Image Source: Google
With this framework, a connection in the midst of the user and the VPN provider, the company of VPN provides protected and private surfing via an encrypted connection, access to many websites and blocked applications, and concealment of establishing the IP address every time the user visits web sites happen.
Some people care deeply about the security of communication that happens on the web so that the service can provide them with a VPN is an advantage for them. These individuals are concerned that the data is sent on the web either the file type or communication happens via VoIP is able to be redeemed by a third party. For professional hackers, access to data is an uncomplicated procedure in the case if your system will not be protected.
A VPN can establish secure communications by using one of the many protocols that contain PPTP, IPSec, and many more so as to create an encrypted tunnel. VPNs also used authentication methods, on top of secure tunnels established encrypted. Before a user can connect to a VPN, a user name and password are required, use a digital certificate, and sometimes even make use of double authentication.
